Quantum technologies can be defined as technologies that, based on quantum mechanics, have capabilities that go beyond what we call classical technology.
These quantum technologies are an emerging field and are based on phenomena such as superposition, entanglement and tunneling.
The interest and relevance of this technology is even shown by the fact that the UN has declared 2025 as the International Year of Quantum Science and Technology.
Main areas of quantum technologies
Quantum technologies are set to enhance aspects not only of science or technology, but also of society by having the ability to change the way we work or live.
These technologies have some main areas. Let’s see what they are and their characteristics.
Quantum computing
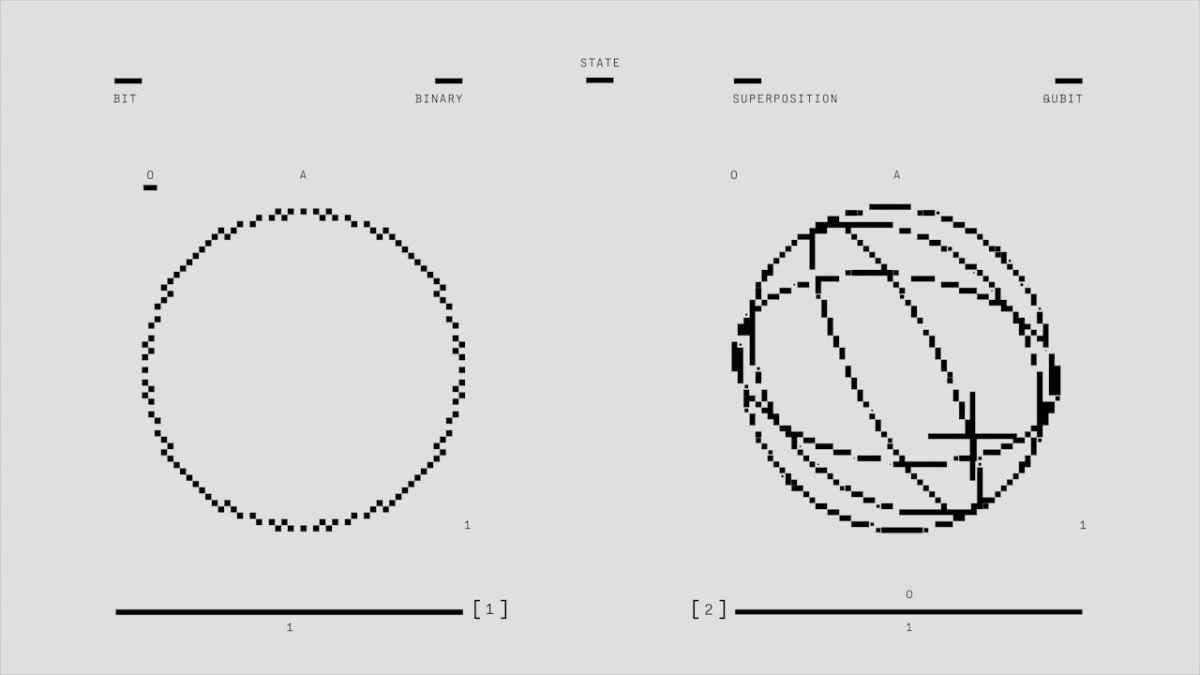
Quantum computing could be defined as computing capable of solving problems so complex that neither traditional computers nor supercomputers can solve them.
Quantum computing is based on quantum bits (or cubits), which, unlike traditional bits, can be in several states at once thanks to a property known as superposition.
Quantum communications
Also based on quantum mechanics, but in this case with a focus on transmitting information efficiently and securely, quantum communications have advanced in recent years, but with the prospect of revolutionising how we transmit and protect information.
Thanks to the entanglement and superposition of particles, a highly secure and efficient connection is generated that has the capacity to overcome the limitations present in classical networks.
Quantum sensors
Also based on quantum mechanics, this type of sensor achieves measurements with unprecedented precision. These devices have an impact in fields such as science and industry, thanks to their ability to detect extremely weak signals, as well as to develop measurements with enormous precision.
As this is a rapidly and constantly evolving field, it is expected to have great potential for growth in the near future. This evolution may make them smaller, cheaper and also more accessible, which will broaden their potential applications.
Thus, we may be looking at devices that reach previously unattainable levels of sensitivity and precision.
Quantum simulation
Also based on quantum mechanics, simulation uses controllable quantum systems to study and shape other complex quantum systems.
Quantum simulation was proposed in 1982 by the American theoretical physicist Richard Feynman, and there are two main types: digital quantum simulators (whose general purpose is to simulate any quantum system) and analogue quantum simulators (designed to simulate how a specific quantum system behaves).
Quantum cryptography
This type of cryptography relies on quantum physics to create messages that are indecipherable except to the receiver.
It differs from traditional cryptography in that while traditional cryptography is based on mathematics, quantum cryptography relies on physics, as mentioned above.
Also, quantum cryptography is based on the use of photons to transmit keys between the sender and receiver in a process known as QKD (Quantum Key Distribution, a concept we will see later), with its main aspects of use being key transmission, intrusion detection and physics-based security.
The advantages of quantum cryptography make it a promising solution for information security with more robust protection against hypothetical threats. Therefore, this technology is focused on sectors where information security is crucial.
Quantum Key Distribution QKD
From Quantum Key Distribution comes the acronym QKD (Quantum Key Distribution), a secure communication method that uses quantum mechanics to create and share cryptographic keys securely between two different parties.
By means of photons that transmit information, they can detect interception attempts in which only the key is distributed, not the message itself.
As summarised by four of our colleagues in the journal Nature -Antonio Pastor, Jesús Folgueira, Diego López and Rafael Cantó Palancar-, ‘QKD is a technology that makes it possible to generate cryptographic keys reliably and synchronously between two distant points, thus solving the problem of generating and distributing keys for applications. Its principles based on quantum mechanics guarantee the inviolability of the keys, making its use in combination with hardware and software encryption systems optimal.